This post covers configuring Highly Available External Platform Services Controller (PSC) Appliance (SSO). For more information about high availability of vCenter and PSC, please follow my post: VMware vCenter 6 Deployment Possibilities: Topologies and High Availability.
Prerequisties and notes to build a highly available External Platform Services Controller
- Load Balancer, VMware supports only: Citrix Netscaler, F5 Networks
or VMware NSX. (please check comments) - With vCenter 6.0, connectivity to the Platform Services Controller is stateful (load balancer as a failover only).
- Set load balancer up for the two PSCs on ports 389, 443, 636, 2012, 2014, 2020.
- VMware-psc-ha-6.0.0.2503195.zip available here.
There are some scalability limitations as well:
- Maximum Platform Services Controllers (PSC) per domain: 8
- Maximum PSCs per vSphere Site, behind a single load balancer: 4
- Maximum objects withiun a vSphere domain (Users, groups, solution users): 1,000,000
- Maximum number of VMware solutions connected to a single PSC: 4
- Maximum number of VMware products/solutions per vSphere domain: 10
Platform Services Controller Type Deployment Considerations
Platform Services Controller can be deployed in the following configurations:
- as an embedded Platform Services Controller
- as an external Platform Services Controller
For simple sites (without Enhanced Linked Mode) is recommended to use an vCenter with embedded Platform Services Controller. High availability is provided by VMware HA because there is only one virtual machine (vCenter + PSC).
For more complex sites it is recommended to use external Platform Service Controllers. Depending on size of infrastructure (how many VMware solutions e.g. vCenters you use) you would use:
- Two to four VMware solutions – single PSC or 2 PSCs with single load balancer.
- Four to eight VMware solutions – 2 PSCs or 4 PSCs with 2 load balancers (2 PSCs behind of each load balancer).
- Eight to ten VMware solutions – 3 PSCs or 6 PSCs with 3 load balancers (2 PSCs behind of each load balancer).
You can also repoint your vCenter 6 to other external Platform Services Controller - also highly available shown in this post.
Configuring Highly Available External Platform Services Controller Appliance
Deploy two External Platform Services Controllers
To deploy Highly Available External Platform Services Controller Appliance please follow the below steps:
- Please deploy the first Platform Services Controller Appliance following steps mentioned here.
- When you deployed the first Platform Services Controller, please deploy the second using again steps mentioned above but with the diffrence mentioned in the following steps 3 and 4.
- In the Set up Single Sign-on tab, please select Join an SSO domain in an existing vCenter 6.0 platform services controller. Type FQDN or IP of thr first PSC you have deployed in step 1. Click Next.
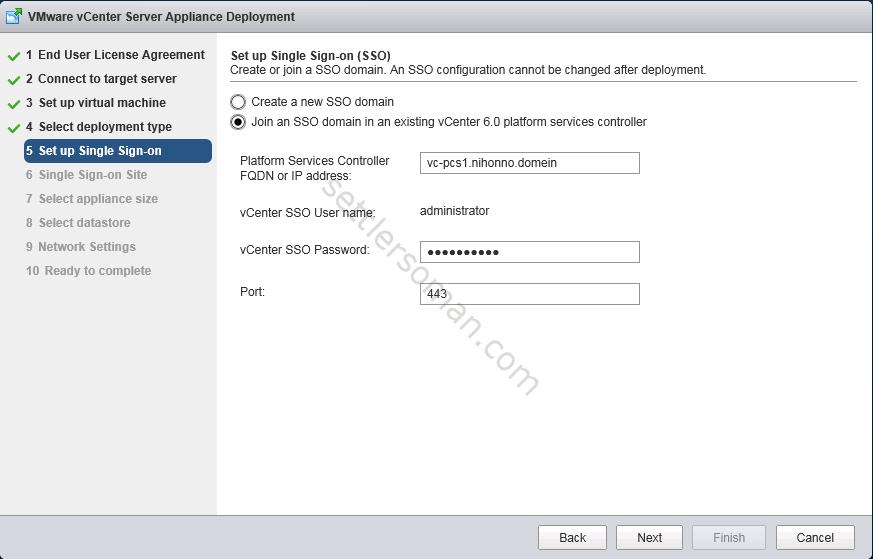
- Select Join an existing site and select SSO site from the list. Click Next.
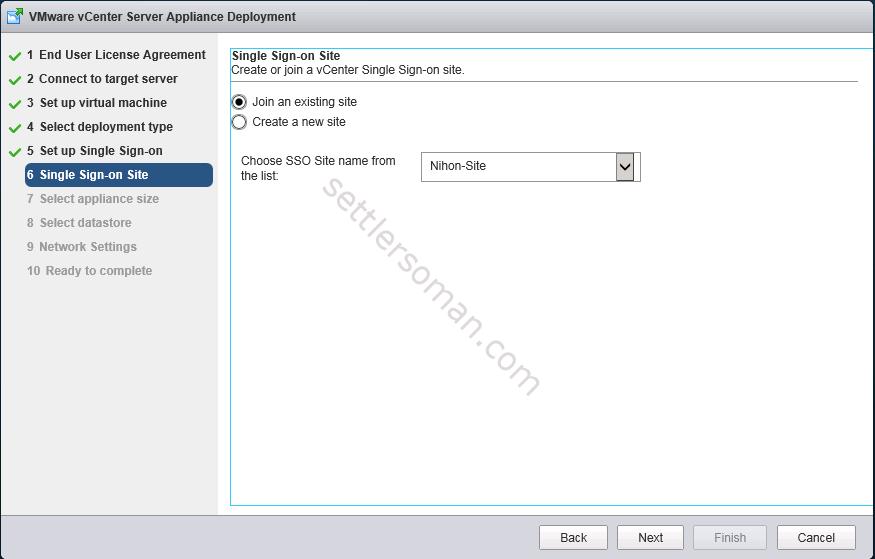
- Follow the rest steps as mentioned in my another post.
- The summary of the second PSC. The Single Sign-On instance IP should be the IP or FQDN of the first PSC.
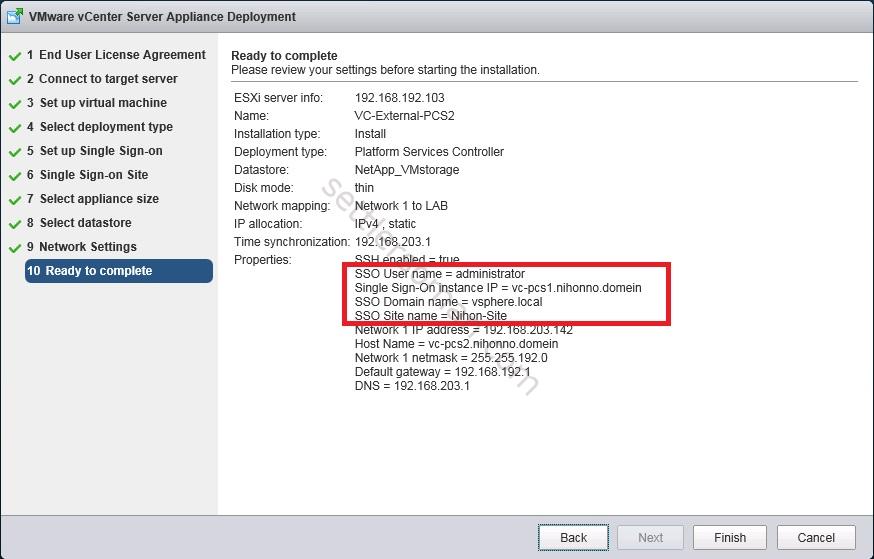
Configuring Platform Services Controllers HA
Now, as you have deployed two External Platform Services Controller Appliances, it's time to configure HA. Please follow the below steps:
- Download the vCenter Single Sign-On high availability configuration scripts from the vCenter Server product download page mentioned in prerequisites earlier in this post.
- Connect to the first and second Platform Services Controller via SSH.
-
On both please,type:
shell.set --enabled True
-
On both please create a catalog name sso-ha:
mkdir /sso-ha
-
Send the above zip file to the PSC via scp.
scp VMware-psc-ha-6.0.0.2503195.zip root@FQDN_of_PSC:
Note: To be able to send files via scp, you need to change shell to bash
chsh -r "/bin/bash" root
If you do not change the shell, you will get the following error:
Unknown command: `scp'
-
On the first PSC, extract the vCenter Single Sign-On high availability scripts to /sso-ha.
unzip VMware-psc-ha-6.0.0.2503195.zip -d /sso-ha/
-
Change directory to /sso-ha on the first PSC:
cd /sso-ha
-
Run the following command on the first PSC:
python gen-lb-cert.py --primary-node --lb-fqdn=loadbalancerFQDN
In my case:
python gen-lb-cert.py --primary-node --lb-fqdn=Nihon-lb.nihonno.domein
You should get the following output:
Initialization complete
executing certTool command
executing certTool command
Using config file : /usr/lib/vmware-vmca/share/config/certool.cfg
Status : Success
Executing openssl command
Executing openssl command
writing RSA key
Modifying hostname.txt
modifying server.xml
Executing StopService --all
INFO:root:Service: vmware-syslog-health, Action: stop
INFO:root:Service: applmgmt, Action: stop
INFO:root:Service: vmware-cis-license, Action: stop
INFO:root:Service: vmware-syslog, Action: stop
INFO:root:Service: vmware-sca, Action: stop
INFO:root:Service: vmware-cm, Action: stop
INFO:root:Service: vmware-rhttpproxy, Action: stop
INFO:root:Service: vmware-stsd, Action: stop
INFO:root:Service: vmware-sts-idmd, Action: stop
INFO:root:Service: vmcad, Action: stop
INFO:root:Service: vmdird, Action: stop
INFO:root:Service: vmafdd, Action: stop
Executing StartService --all
INFO:root:Service: vmafdd, Action: start
INFO:root:Service: vmware-rhttpproxy, Action: start
INFO:root:Service: vmdird, Action: start
INFO:root:Service: vmcad, Action: start
INFO:root:Service: vmware-sts-idmd, Action: start
INFO:root:Service: vmware-stsd, Action: start
INFO:root:Service: vmware-cm, Action: start
INFO:root:Service: vmware-cis-license, Action: start
INFO:root:Service: vmware-sca, Action: start
INFO:root:Service: applmgmt, Action: start
INFO:root:Service: vmware-syslog, Action: start
INFO:root:Service: vmware-syslog-health, Action: start
Copy the contents of the /ha to the other nodes
Please copy the p12 file into the F5 loadbalancer
Please copy the lb_rsa.key file and lb.crt file into the Netscaler loadbalancer -
Create a forward and reverse DNS entry for the VIP created to load-balance the Platform Services Controller traffic.
-
On the second PSC, please create the following folders:
mkdir /ha
mkdir /ha/keys -
Copy the /sso-ha and /ha folder from the first Platform Services Controller. Please run the following command on the primary (first) PSC:
scp /sso-ha/* root@FQDN_2nd_PSC:/sso-ha
scp /ha/* root@FQDN_2nd_PSC:/haIn my case:
scp /sso-ha/* root@vc-psc2.nihonno.domein:/sso-ha
scp /ha/* root@vc-psc2.nihonno.domein:/ha -
Copy /etc/vmware-sso/keys/ from the first Platform Services Controller to /ha/keys on the second PSC.
scp /etc/vmware-sso/keys root@FQDN_2nd_PSC:/ha/keys
In my case:
scp /etc/vmware-sso/keys root@vc-psc2.nihonno.domein:/ha/keys
-
On the second PSC, change directory to /sso-ha.
cd /sso-ha
-
Run the following command on the second PSC:
python gen-lb-cert.py --secondary-node --lb-fqdn=loadbalancerFQDN --lb-cert-folder=/ha --sso-serversign-folder=/ha/keys
In my case:
python gen-lb-cert.py --secondary-node --lb-fqdn=nihon-lb.nihonno.domein --lb-cert-folder=/ha --sso-serversign-folder=/ha/keys
-
On first Platform Services Controller, update the endpoint URL by running:
python lstoolHA.py --hostname=FQDNofLocalMachine --lb-fqdn=loadbalancerFQDN --lb-cert-folder=/ha --user=Administrator@SSODomain
In my case:
python lstoolHA.py --hostname=vc-psc1.nihonno.domein --lb-fqdn=nihon-lb.nihonno.domein --lb-cert-folder=/ha --user=Administrator@vsphere.local
-
Follow the steps mentioned here to install a new external vCenter Server. When asked for the Platform Services Controller, enter the FQDN of the load balancer VIP.
