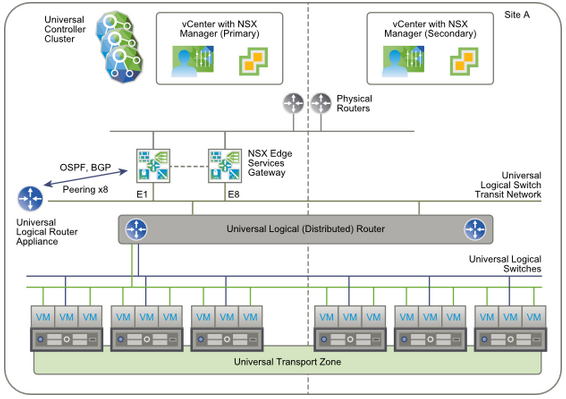
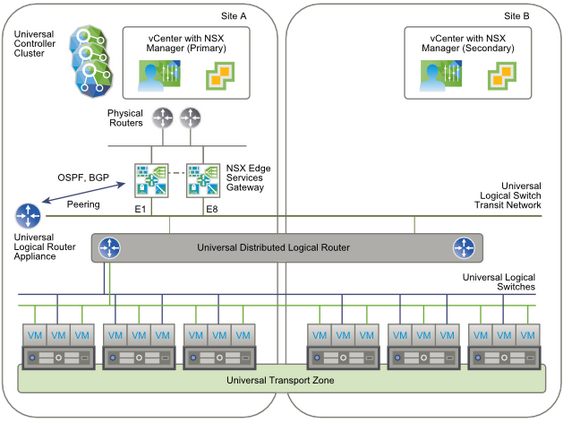
In August, VMware released NSX 6.2 with some new features. One of them is Cross-vCenter Networking and Security that I would like to discuss. In this post you can find the following info:
- Overview of Cross-vCenter Networking and Security.
- Cross-vCenter NSX Topologies.
- Cross-vCenter components.
- Cross-vCenter benefits.
Cross-vCenter Networking and Security feature was designed for environments where you can find multiple sites (single as well) with multiple vCenter Servers. Every vCenter Server is paired with its own NSX Manager (relation 1:1). However one NSX Manager is assigned the role of primary NSX Manager and the others - secondary. You can have one primary with max 7 secondary NSX Managers. The primary NSX Manager is responsible for:
- Deployment a universal controller cluster (available only on the primary) providing the control plane for the Cross-vCenter NSX environment.
- Creation of universal objects such as universal logical switches, universal transport zones, universal distributed routers, universal firewall rules.
All above objects are synchronized to the secondary NSX Managers but you can edit these objects only on the primary NSX Manager. You can also create local objects (transport zones, logical switches or logical routers etc.) and they will be visible only on NSX "owner" 🙂
There are two Cross-vCenter NSX topologies:
- Single or Multi-Site.
- Local Egress.
In single or multi-site Cross-vCenter NSX environment you have to create a universal transport zone including all clusters in the site or sites and attached universal logical switches. On the primary NSX (site) you have a universal logical router with an NSX Edge appliance (edge services gateways (ESG), max 8) to enable dynamic routing. Edge appliances are connected to the transit network and the physical egress router network.
In Local Egress topology you customize routes at the universal logical router, cluster and host level. The edge services gateways (ESGs) in each site have a default route that sends traffic out through that site's (=local) physical routers. The universal logical router is configured with two appliances, one in each site and those appliances learn routes from local ESGs. Then the learned routes (with local ID) are sent to the universal controller cluster located on the primary site (NSX Manager). The universal controller clusters sends routes learned to the hosts located in specific site: routes learned on the site A are sent to the hosts in site A and routes learned on the site B are sent to the hosts in site B.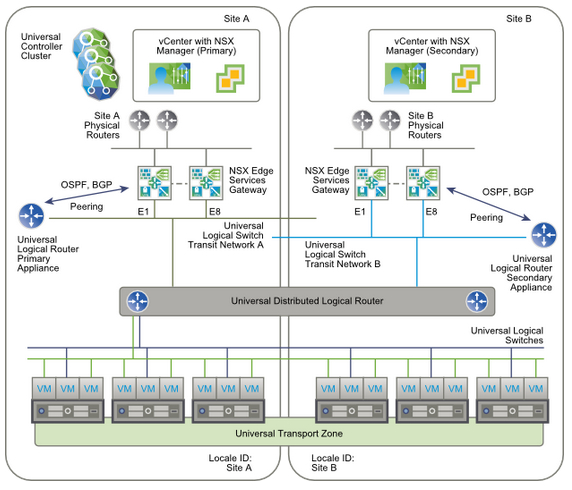
For more information e.g. how to configure Cross-vCenter NSX, please follow VMware NSX Documentation Center.
Conclusion
Cross-vCenter NSX provides centralized management of universal objects and vMotion across vCenter Servers without re-configuring VMs. It also provides enhanced disaster recovery because Site Recovery Manager 6.1 automatically recognizes that VMs are connected to the port groups in Universal Logical Switches so manual network mapping between the protected and recovery sites is not required.